jeffro256's new vulnerability disclosure highlights 'high severity' bug patched in Monero v0.18.2.2
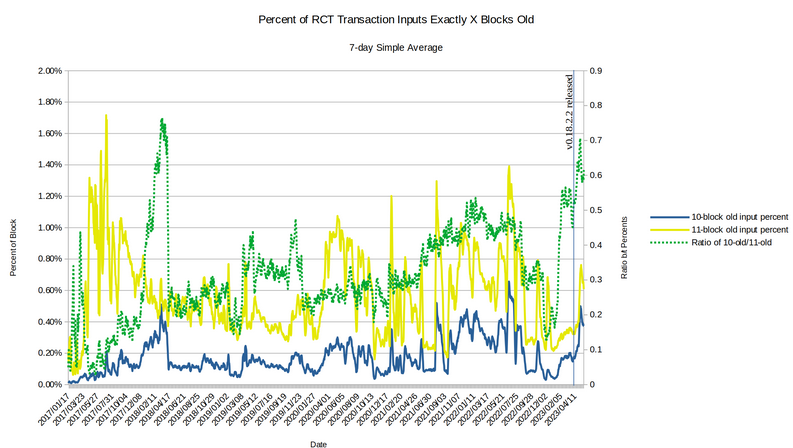
jeffro2561 posted a new vulnerability disclosure (Post-Mortem of 10-Block-Old Decoy Selection Bug 20232) which emphasizes the critical importance of the latest Monero software release (v0.18.2.23):
[..] in the gamma picker code, there was a off-by-one bug that didn’t allow the gamma picker to pick decoys which are exactly 10 blocks old. The wallet can, however, still spend owned outputs that are exactly 10 blocks old. This means that an external observer can guess the true spend of an input ring with very high likelihood if one of the ring members is exactly 10 blocks old.
The long-standing bug was stumbled upon by accident while attempting to fix an infinite while loop during decoy selection in PR #87944.
Unfortunately, due to communication issues5 between Monero developers, the release was not marked recommended update and third-party wallets were not immediately notified.
Vulnerability Overview
Severity: HIGH
Affected versions: GUI/CLI wallet versions v0.14.1.0 to v0.18.2.1
Impact: Loss of sender anonymity for transactions spending funds exactly 10 blocks old
What to do: Update wallet to v0.18.2.2
Users that are forced to run older wallet versions (<0.18.2.2) can apparently6 avoid the privacy loss by waiting at least 1 extra block before spending unlocked funds.
This is an ongoing story and the report will be updated when new information is available.